Automated teller machines (ATM) have always a been a big target for criminals. In the past, hunting for ATMs included some heavy duty tools like a cutting torch or explosives. However with the dawn of the Digital Age, everything has changed. Today, criminals can ‘jackpot’ an ATM without the need for special equipment.
At the recent SAS 2016 conference Olga Kochetova, a penetration-testing specialist at Kaspersky Lab explained why ATM’s are so vulnerable, in her talk entitled ‘Malware and non-malware ways for ATM jackpotting.’
1. First of all, ATM’s are basically computers. They consist of a number of electronic subsystems, including some exotic industrial controllers, but there’s always a conventional PC in the very centre of ATM’s system.

2. Moreover, it’s very likely that this PC is controlled by a rather old operating system like Windows XP. You probably know what is wrong with Windows XP: it is not supported by Microsoft any more, so any vulnerability found after support was killed off is a perpetual zero-day that no-body will ever patch. And you can bet that there’s A LOT of these vulnerabilities.
#Microsoft is ending support for Windows XP. Learn what this means for your Kaspersky Lab products. http://t.co/j90rhV8wY3
— Kaspersky (@kaspersky) January 21, 2014
3. Besides, it’s also very likely, that there’s a lot of vulnerable software running in ATM’s system. From some outdated flash players with over 9000 widely known bugs inside to remote administration tools and more.
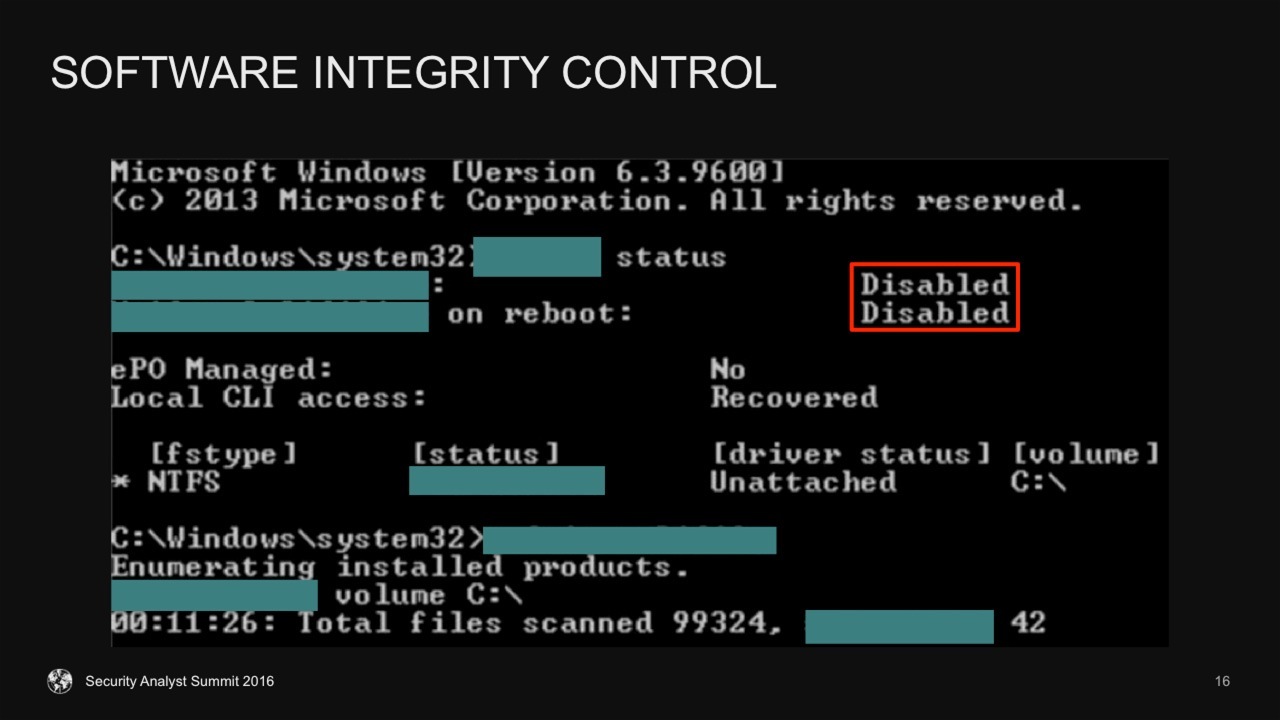
4. ATMs manufacturers tend to believe that ATM’s are always operating in ‘normal conditions’ and nothing ever goes wrong. Hence there’s usually no software integrity control, no antivirus solutions, no authentication of an app that sends commands to cash dispenser.
5. In contrast to cash deposit unit and money dispenser, which are always pretty carefully armoured and locked, the PC part of an ATM is easily accessible. Its enclosure is usually made of plastic, thin metal at best, and secured with locks too simple to keep criminals at bay. The logic of ATM’s manufacturers is as following: if there’s no money in this part of an ATM, why bother to keep it secure?
RT @GrzegorzBr: Dozens of banks lose millions to cybercriminals attacks #theSAS2016: https://t.co/9lOgLiRMd6 via @kaspersky
— Kaspersky (@kaspersky) February 8, 2016
6. Modules of ATM’s are interconnected with standard interfaces, such as COM and USB ports. Sometimes these interfaces are accessible from outside of the cabinet. Even if not, you still need to keep in mind previous issue.
Infected USB drive idled power plant for 3 weeks http://t.co/3TwQFxNr
— Eugene Kaspersky (@e_kaspersky) January 18, 2013
7. By their very nature, ATM’s must be connected — and they always are. Since the Internet is the cheapest way of communicating these days, banks use it to connect ATM’s to processing centres. And guess what? Yes, you can find ATM’s on Shodan!
#Shodan shows thousands of exposed ATMs potentially vulnerable to a network attack @_endless_quest_ #TheSAS2016 pic.twitter.com/9E3SSYwG89
— Eugene Kaspersky (@e_kaspersky) February 9, 2016
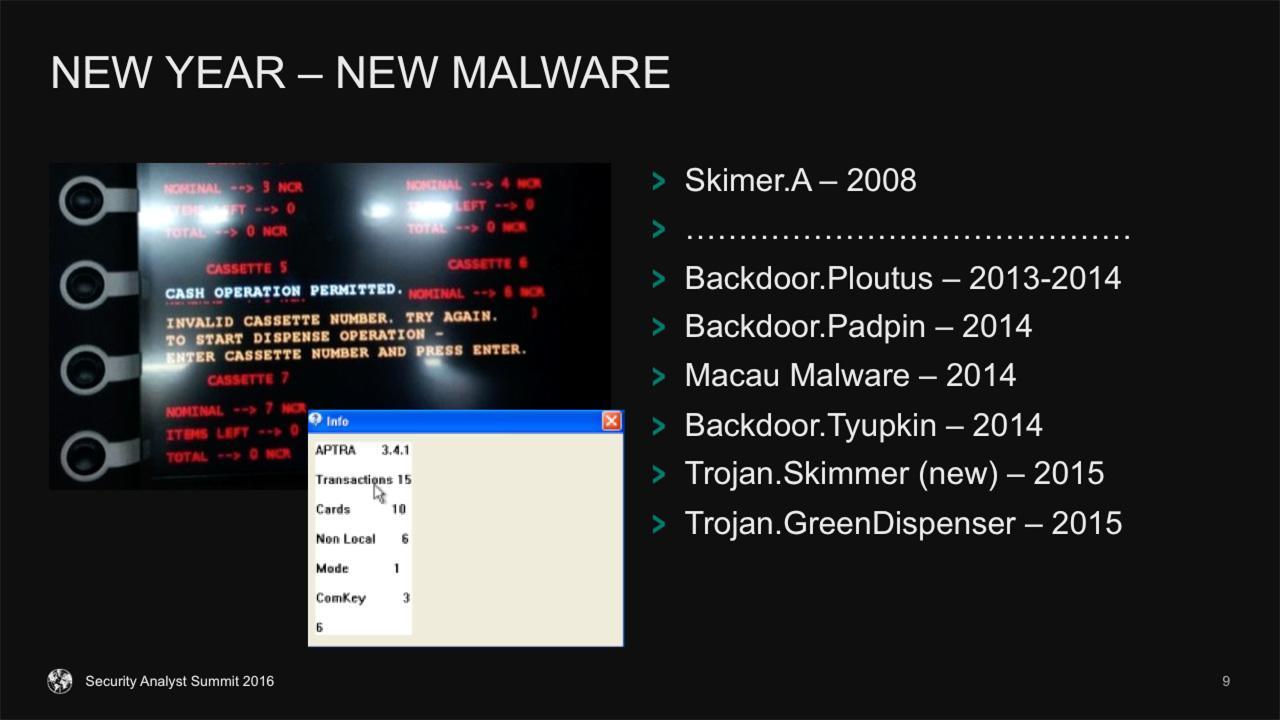
Considering all the above mentioned issues, there are a plenty of opportunities for criminals. For example, they can write a piece of malware, install it on the ATM’s system and cash out. Such trojans specially crafted for ATM’s emerge regularly. For example, about a year ago we discovered one of them called Tyupkin.
Another way is to use some additional hardware that can be attached to ATM’s USB port. For their proof-of-concept Olga Kochetova and Alexey Osipov used a cheap and tiny single-board computer Raspberry Pi equipped with a Wi-Fi adapter and a battery. Watch the video below to see what happens next.
The attack through the World Wide Web can be even more dangerous. Culprits can establish fake processing centres, or seize a real one. In this case criminals can rob lots of ATM’s without even getting physical access to their hardware. That is exactly what One-Billion-Hackers from the Carbanak group managed to achieve: they had obtained control over critical PCs in banks’ networks and after that they were able to send commands to ATM’s directly.
Full report on the #Carbanak APT is now live http://t.co/KRmjD1GhyL via @Securelist pic.twitter.com/5OMzJE0DgS
— Kaspersky (@kaspersky) February 16, 2015
All in all, banks and ATM’s manufacturers should be more concerned about security of banking machines. They need to reconsider both software and hardware security measures, make a safer network infrastructure and so on. It’s also important for banks and manufacturers to react quicker to threats and to intensively collaborate with law enforcement agencies and security companies.
 ATMs
ATMs

 Tips
Tips