Typically we don’t cheer bugs. However, today we’ll make an exception.
You see a bug or flaw in the code for Petya ransomware has allowed a developer to create a tool to unlock a user’s device without paying the ransom.
Last month, we alerted you about Petya and it’s pension to destroy devices. So I’d say that a cheer or Internet high-five is well deserved for the user identified as @Leostone on Twitter.
Hurray!!! Its official, the found key is working!!!
I'll update the github with the genetic version, keys will be found in less than a min:)— leostone (@leo_and_stone) April 8, 2016
With the avatar being an egg, one would have to wonder – does this decryptor actually work? To find out, we reached out to our research team.
The team confirmed that the tool actually works. Since they had previously built a similar tool to decrypt CoinVault and Bitcryptor, we asked them if they’d be making another decryptor. They replied, “no, because everything is made in Goprograming language and is using a third party genetic algorithm library. In order to make our own utility, we would have to reverse engineer and rewrite the program. This is a lot of work.”
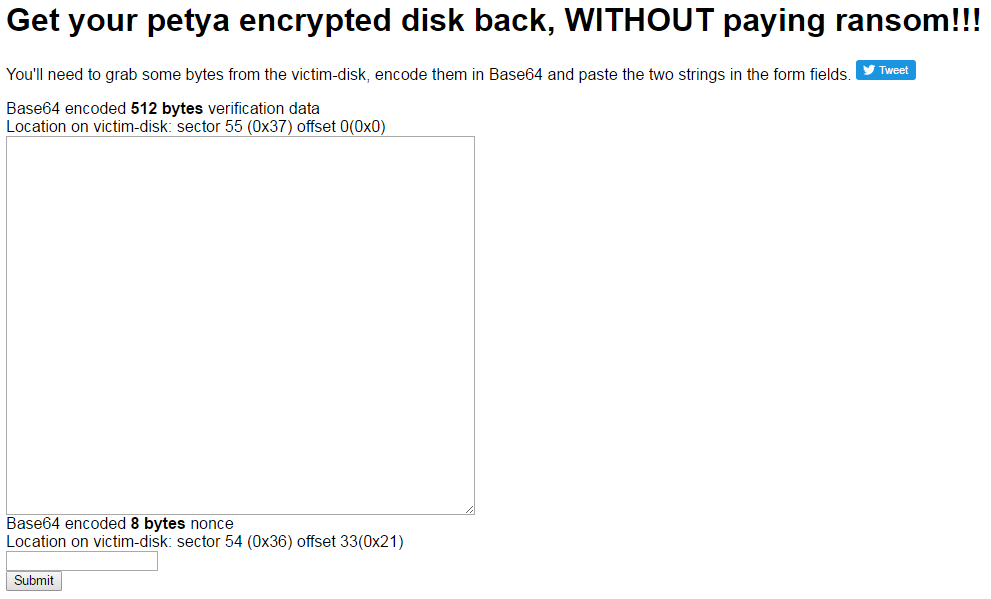
The team then close the chat by noting that this tool exploits a flaw in the Petya programming. Much like companies with patches, the researchers note that in a week or so, we will see a newer revision of Petya that fixes the flaw that allows the data to be decrypted.
If you’ve fallen victim to Petya and don’t want to pay the ransom of approximately $480, you may want to give the tool a try, you can access the site here.
 Patya Ransomware
Patya Ransomware
