Can you imagine a world where, every time you wanted to go somewhere, you had to reinvent the wheel and build a bicycle from scratch? We can’t either. Why reinvent something that already exists and works perfectly well? The same logic applies to programming: developers face routine tasks every day, and instead of inventing their own wheels and bicycles (which might even be not up to par), they simply grab ready-made bicycles code from open-source GitHub repositories.
This solution is available to anyone — including criminals who use the world’s best free open-source code as bait for attacks. There’s plenty of evidence to back this up, and here’s the latest: our experts have uncovered an active malicious campaign, GitVenom, targeting GitHub users.
What is GitVenom?
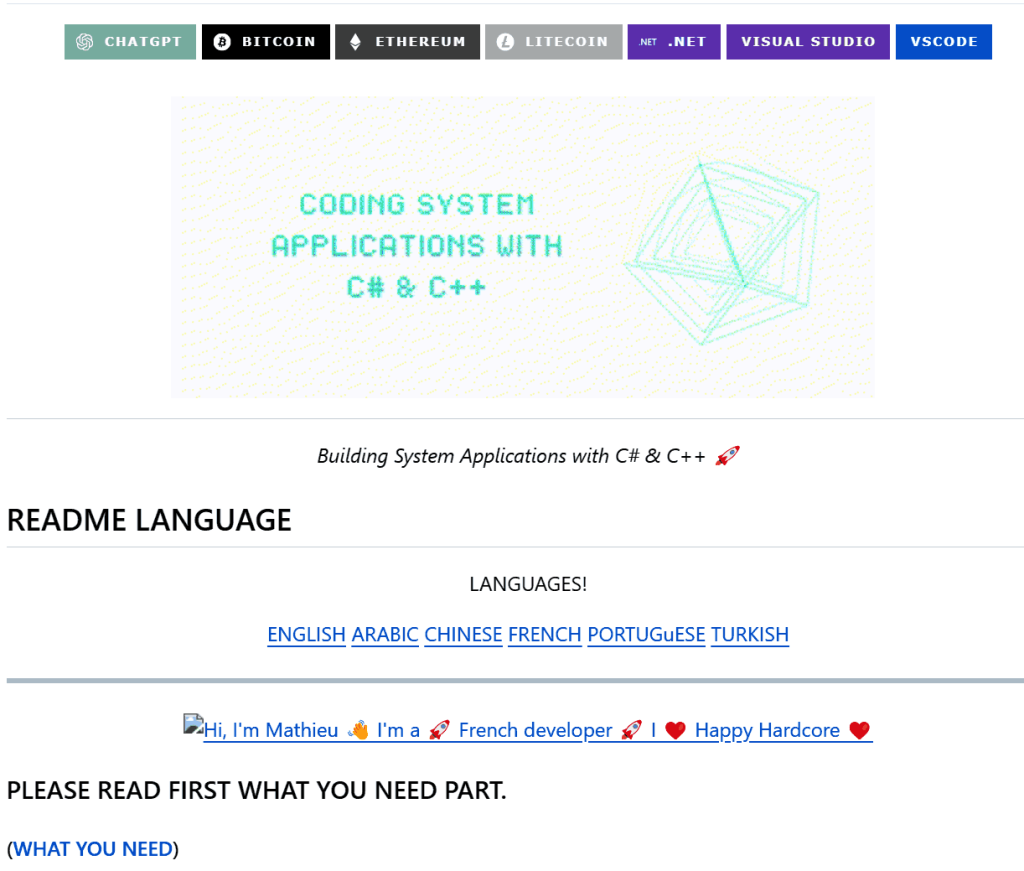
GitVenom is what we named this malicious campaign, in which unknown actors created over 200 repositories containing fake projects with malicious code: Telegram bots, tools for hacking the game Valorant, Instagram automation utilities, and Bitcoin wallet managers. At first glance, all the repositories look legitimate. Especially impressive is the well-designed README.MD file — a guide on how to work with the code — with detailed instructions in multiple languages. In addition to that, attackers added multiple tags to their repositories.
Another indicator reinforcing the apparent legitimacy of these repositories is the large number of commits. The attackers’ repositories have tons of them — tens of thousands. The attackers weren’t, of course, manually updating each of the 200 repositories to maintain authenticity, but simply used timestamp files that updated every few minutes. The combination of detailed documentation and numerous commits creates the illusion that the code is genuine and safe to use.
GitVenom: Two years of activity
The campaign started a long time ago: the oldest fake repository we found is about two years old. In the meantime, GitVenom has affected developers in Russia, Brazil, Turkey, and other countries. The attackers covered a wide range of programming languages: malicious code was found in Python, JavaScript, C, C#, and C++ repositories.
Regarding the functionality of these projects, the features described in the README file didn’t even match the actual code — in reality, the code doesn’t do half of what it claims. But “thanks” to it, victims end up downloading malicious components. These include:
- A Node.js stealer that collects usernames and passwords, crypto wallet data, and browser history, packages the stolen data into a .7z archive, and sends it to the attackers through Telegram.
- AsyncRAT — an open-source remote administration Trojan, which can also function as a keylogger.
- Quasar — an open-source backdoor.
- A clipper that searches the clipboard for crypto wallet addresses and replaces them with attacker-controlled addresses. Notably, in November 2024, the hacker wallet used in this attack received a one-time deposit of about 5 BTC (approximately US$485,000 at the time of the study).
You can read more about the details of this malicious campaign in our full research published on SecureList.
How to protect yourself from malicious code on GitHub
In short, the best defense is vigilance. Since over 100 million developers use GitHub, attackers will likely continue to spread malicious code through this popular platform. The only question is how they’ll do it — a decade ago, no one imagined that attackers would be able to conduct campaigns like GitVenom for so long and with such persistence. Therefore, every developer should maintain their cybersecurity hygiene when working with GitHub.
- Analyze code before integrating it into an existing project.
- Use malware protection on both computers and smartphones.
- Check less obvious indicators carefully: contributor accounts, the number of stars (likes), and the project creation date. If the account was created three days ago, the repository two days ago, and it only has one star, there’s a good chance the project is fake and the code is malicious.
- Don’t download files from direct links to GitHub shared in chats, suspicious channels, or on unverified websites.
- If you find a suspicious repository, report it to GitHub — this could save others’ devices not protected with a Kaspersky Premium.
 GitHub
GitHub

 Tips
Tips