You may have noticed a slight drop in the amount of coverage of ransomware on our Kaspersky Daily blog in recent years. Sadly, it’s not that ransomware attacks have stopped. Far from it — such incidents are now so commonplace that they’ve become part of the cyber-furniture. Nevertheless, some ransomware attacks still have the power to shock. In this post, we take you through the ransomware incidents of 2024 that made a lasting impression in terms of scale, impact, or mode of attack…
January 2024: ransomware attack on Toronto Zoo
One of the first major ransomware incidents of 2024 was the January attack on Canada’s biggest zoo, located in Toronto. The zoo’s management was quick to reassure the public that no systems related to animal care were impacted. Indeed, its website and ticketing service were also unaffected, so the zoo continued to welcome visitors as usual.
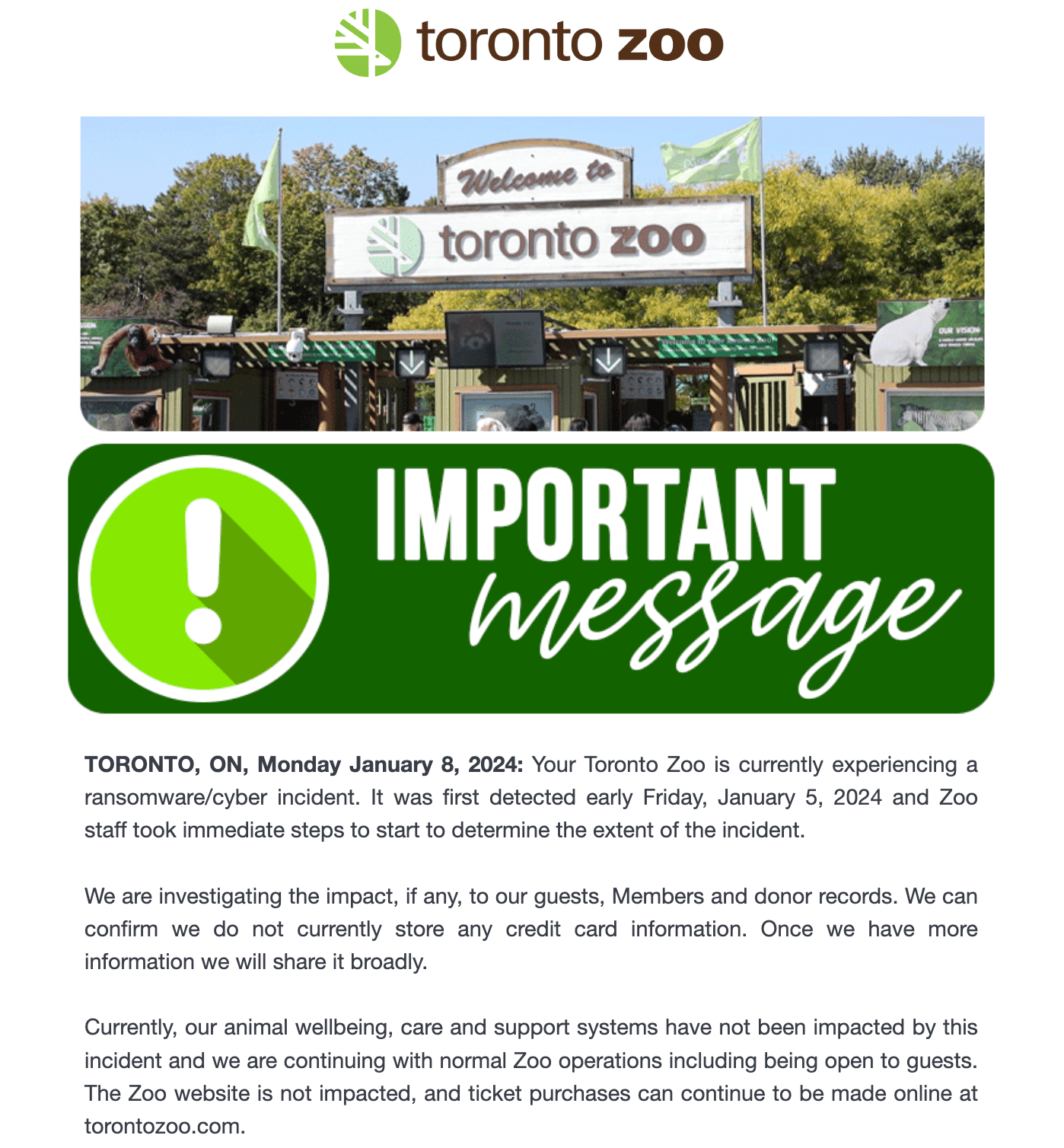
The official Toronto Zoo website reports a cyberattack and assures that all animals are fine. Source
It soon transpired that the attackers had stolen a significant amount of zoo employees’ personal information — dating back to 1989. This incident served as yet another reminder that even organizations far removed from critical sectors can become targets of ransomware attacks.
February 2024: $3.09 billion attack on UnitedHealth
February’s attack on the U.S. healthcare insurance giant UnitedHealth would easily claim the “ransomware incident of the year” award if such existed. The attack was in fact carried out on Optum Insight, a UnitedHealth subsidiary that provides technology-enabled services.
Getting granular here, the direct target was Change Healthcare, which has been part of Optum since 2022. This company’s platform serves as a financial intermediary between payers, patients, and healthcare providers. The attack took down over a hundred different Optum digital services. As a result, UnitedHealth was able to process neither electronic payments nor medical applications. Essentially, the company couldn’t perform its core function — causing chaos across the U.S. healthcare system.
The attack’s repercussions were so extensive that UnitedHealth even set up a dedicated website to provide updates about the process of restoring the company’s affected IT systems. The bulk of the restoration work was carried out in the first months after the attack. However, almost a year on, the site continues to post regular updates, and some systems still have the “service partially available” status.
A few days after the attack, the ransomware gang BlackCat/ALPHV claimed responsibility. In addition, they reported stealing 6TB of confidential data — including medical records, financial documents, personal data of U.S. civilians and military personnel, and a wealth of other sensitive information.
UnitedHealth ended up paying the gang a $22 million ransom. And it’s rumored that the company had to pay up again when BlackCat’s accomplices from the RansomHub group claimed they hadn’t received their share and began leaking the stolen data into the public domain.
However, compared to the total financial losses caused by the incident, the ransom was a mere drop in the ocean. UnitedHealth’s own financial reports estimate the damage in Q1 alone at $872 million. As for the total damage for the year 2024, it reached an eye-watering $3.09 billion.
According to the latest reports, the attackers stole medical data of more than 100 million patients, which is approximately one in three U.S. residents!
March 2024: Panera Bread’s week-long outage
In March, ransomware attackers targeted U.S. food-chain giant Panera Bread. The incident knocked out many of its IT systems, including the online ordering service, offline payment system, telephony, website and mobile apps, loyalty program, various internal systems for employees, and other services.
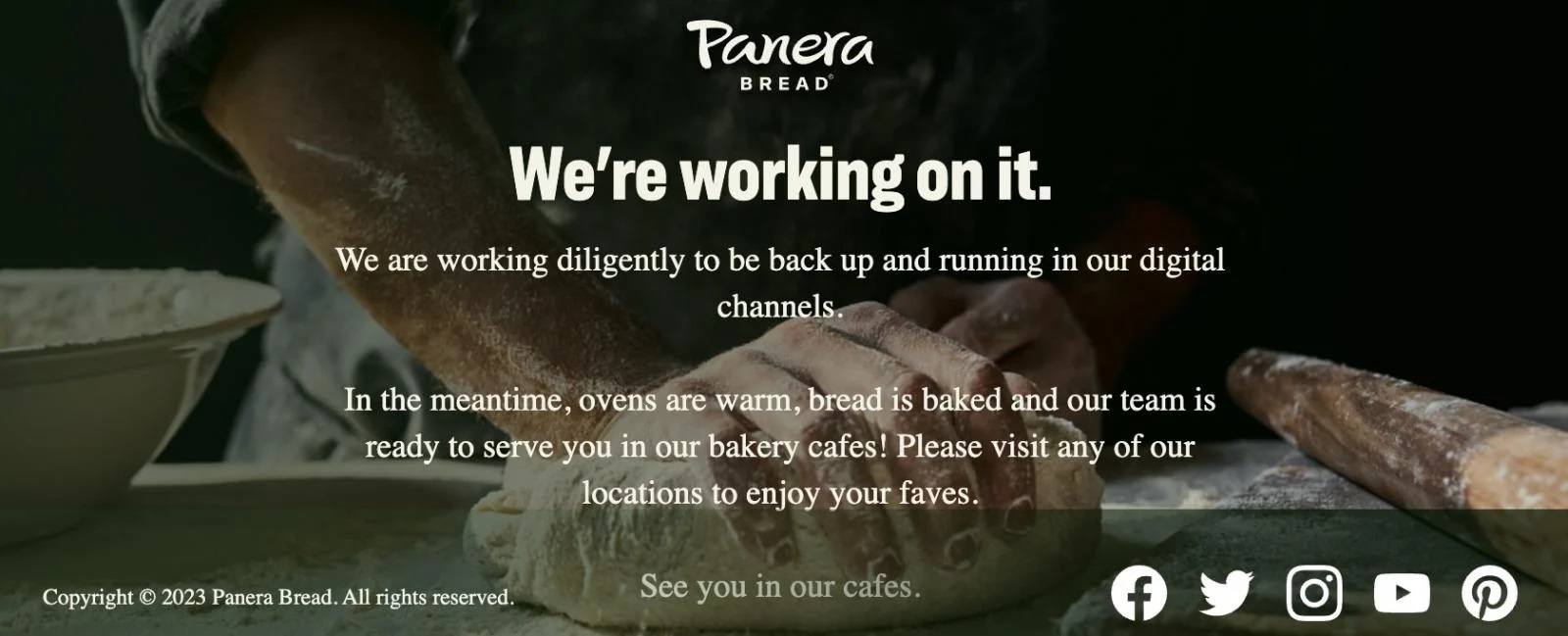
Stub message on the Panera Bread website. Source
Over 2000 restaurants in the Panera Bread chain continued to operate after the attack — but in stone-age conditions: payment was by cash only; subscription offers (such as unlimited drinks for $14.99 per month) were temporarily unavailable; loyalty program points weren’t awarded; and restaurant staff had to manually coordinate their work schedules with managers. The outage lasted about a week.
During the attack, as we learned three months later, the personal data of Panera Bread employees was stolen. By the looks of it, the company ended up paying a ransom to keep that data from being published.
April 2024: Hunters International attack on Hoya Corporation
Early April saw an attack on Hoya Corporation, the major Japanese optics manufacturer. In an official statement, the company said that the systems of some manufacturing plants, plus the ordering system for several products had been affected.
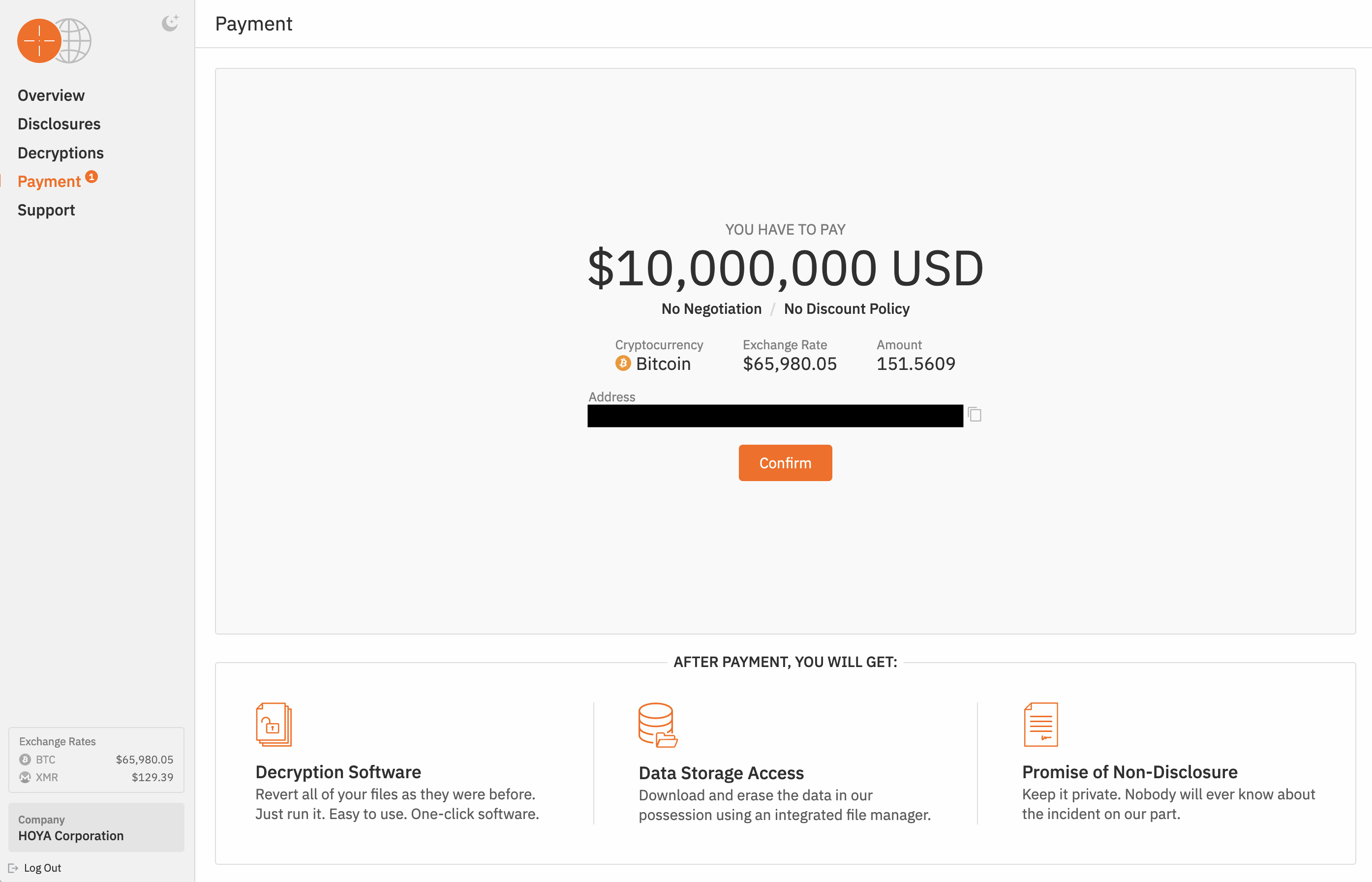
Hunters International demanded a ransom of $10 million (151.56 BTC at the then exchange rate) from Hoya Corporation. Source
A week after the incident, it was confirmed as a ransomware attack. The Hunters International ransomware-as-a-service group’s website reported that the attackers had stolen 1.7 million files from Hoya (around 2TB), and demanded a ransom of $10 million.
May 2024: Major disruptions at U.S. healthcare network Ascension
In early May, Ascension, one of the largest healthcare networks in the United States, had some of its systems taken offline due to a “cybersecurity event”. The “event” in question was soon revealed to be a ransomware attack on the organization’s IT infrastructure. The disruption affected electronic medical records, telephony, and systems for ordering tests, procedures, and medications.
As a result, some hospitals run by Ascension couldn’t admit emergency patients, and had to divert ambulances to other facilities. Healthcare workers also reported having to switch to pen and paper and writing out medical referrals from memory.
Restoring the affected electronic systems took over a month. The Black Basta ransomware group claimed responsibility for the attack. The investigation revealed that the root cause of the attack was an employee who downloaded a malicious file onto a company device.
It was revealed in late 2024 that the cybercriminals had stolen the personal data of 5.6 million patients and hospital staff. This data included medical records, payment details, insurance information, social security and ID numbers, addresses, dates of birth, and more. As compensation, Ascension offered all those affected a free two-year subscription to its identity-theft protection service.
June 2024: Ransomware attack on healthcare provider hits London hospitals
In early June, news broke of a ransomware attack on Synnovis, a UK company providing pathology and diagnostic services to several major London hospitals. As a result, over 800 surgeries were canceled and some patients diverted to other facilities.

Major outage reported on the website of Synnovis, a healthcare provider for several major London hospitals. Source
One of the worst consequences of the attack was that doctors were unable to match donor and patient blood types, forcing them to use the universal blood type O. This quickly led to a shortage.
July 2024: Los Angeles County Superior Court shut down by ransomware
The Los Angeles County Superior Court, the largest single unified trial court in the United States, suspended all 36 courthouses in the county due to a ransomware attack. Both external services (such as the court’s website and the jury duty portal) and internal resources (including the case management system) were impacted.
The Los Angeles courts reopened two days later, but restoring publicly-accessible electronic services took about a week longer. After that, however, the Superior Court stopped updating the public about the incident, so it’s unknown how long it took to restore the courts’ internal systems. It also remains a mystery whether the court paid a ransom or what data the attackers may have gotten away with.
August 2024: Ransomware attack on vodka maker Stoli
In August, a ransomware attack targeted Stoli Group, the producer of Stolichnaya vodka and multiple other beverages. The incident had a serious impact on the company’s IT infrastructure and operations: an ERP system failure meant that all internal processes, including accounting, had to be transferred to manual mode.
In particular, the incident meant that Stoli Group companies couldn’t submit financial statements to creditors — which alleged that the Stoli companies failed to repay a debt of $78 million. Stoli Group had to file for bankruptcy in December.
September 2024: Highline Public Schools closure due to ransomware
In early October, Highline Public Schools, a public school district in the U.S. state of Washington, temporarily closed all 34 of its member schools, which serve more than 17,000 students and employ around 2000 staff. The cyberattack halted all educational activities, including sports events and meetings, for four school days.
About a month after the incident, Highline’s management confirmed that the attack was ransomware-related. Unfortunately, Highline Public Schools officials never disclosed whether any personal information of staff or students had been compromised. As a precaution, however, the district offered all Highline employees one year of free credit and identity monitoring services.
Although the schools were quite quick to reopen, it took a long time to restore the IT infrastructure back to normal operation. Regretfully, more than a month passed before employees and students were finally urged to change their passwords and reinstall the operating system on all school-supplied devices.
October 2024: Ransomware attack on Casio
In early October, Japan’s Casio, the renowned electronics manufacturer, reported unauthorized access to its network. According to its statement, the incident resulted in failure of IT systems and unavailability of certain unspecified services.
Five days later, the ransomware group Underground claimed responsibility for the attack. The group also stole data during the hack, which it posted on its website — including confidential documents, patent information, employees’ personal data, legal and financial documents, project information, and so on. The very next day, Casio confirmed the data theft.
In early 2025, Casio released more details about the number of people whose data had been stolen. According to the company, a total of 8500 people were affected, of which around 6500 were employees, and 2000 were business partners. At the same time, Casio reported not paying a ransom to the attackers and announced that most (but not all) services were already back up and running.
Interestingly, in that same October 2024, Casio was the victim of another successful attack, unrelated to the above ransomware incident.
November 2024: Ransomware attack on Bologna FC
In November, ransomware claimed a rather atypical victim — the Italian soccer club Bologna FC. The club posted on its website an official statement about a ransomware attack, warning that “it is a serious criminal offence” to store or distribute stolen data.
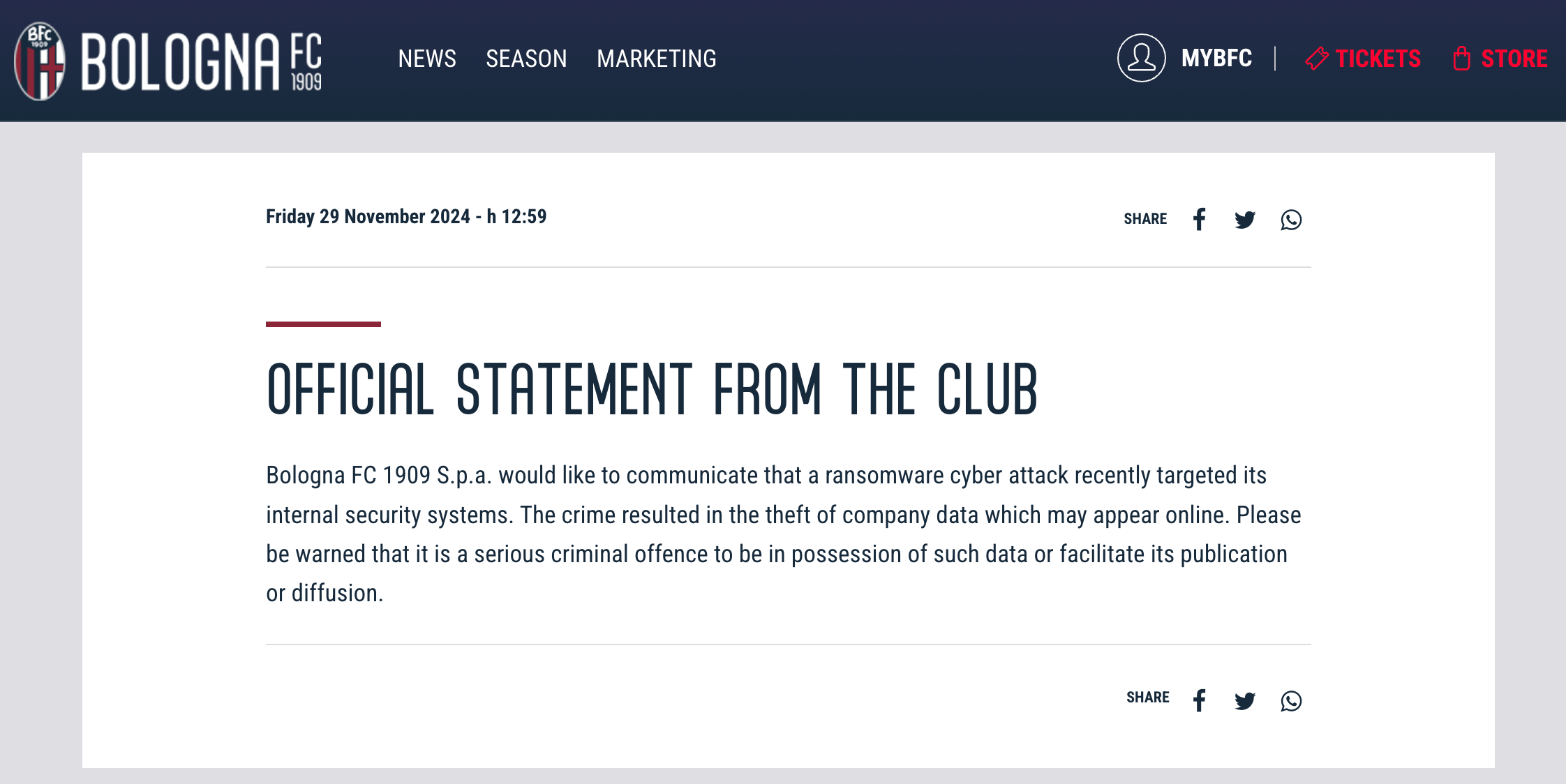
The Italian soccer club Bologna FC website reports a ransomware attack. Source
The RansomHub group claimed responsibility for the hack. Later, it published the stolen data after the club refused to pay the ransom. According to the attackers, the leaked information included sponsorship contracts, the club’s complete financial history, personal and confidential player data, medical records, transfer strategies, confidential data of fans and club employees, and much more.
December 2024: Ransomware attacks medical tissue and equipment supplier Artivion
In December, Artivion, a global supplier of tissues and equipment for cardiac surgery, announced that its IT infrastructure had been compromised by a cyberattack. The attackers encrypted some of the company’s systems and stole data from affected computers.
According to Artivion, the incident caused “disruptions to some order and shipping processes”, as well as corporate operations. The company also reported being insured against such incidents, but the policy may not fully cover the damage caused by the attack.
How to defend against ransomware attacks
Ransomware continues to evolve, and every year the attacks take on new, complex forms. Therefore, in today’s world, effective protection against ransomware requires a comprehensive approach. We recommend the following security measures:
- Provide training courses for employees so they can learn about the basics of cybersecurity.
- Implement proper data storage and employee access
- Back up data regularly, and keep the backups in network-isolated storage.
- Install reliable protection on all corporate devices.
- Use an XDR solution to monitor suspicious network activity.
- Outsource threat detection and response to a specialist company if your in-house information-security service lacks the resources for it.
 anti-ransomware
anti-ransomware

 Tips
Tips