Recent developments in the smartphone world and the emergence of mobile apps for almost every use have inevitably led to increased smartphone and tablet usage when dealing with sensitive data. Be it your CV on LinkedIn, private pictures sent to your lover via WhatsApp, Viber or other similar app, one-time passwords for online banking – you send and receive such data on your mobile device. Unfortunately, most people don’t realise how often and how easily that data, which you would never trust to most people around you, could be intercepted by a complete stranger seated ten metres away.
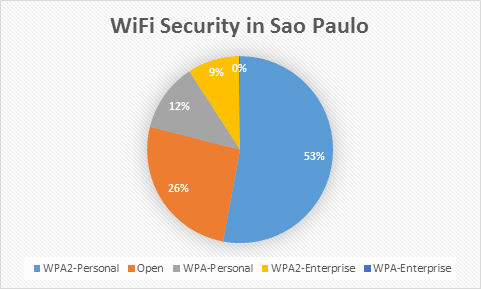
The main pieces of this insecurity puzzle are underprotected Wi-Fi and lack of security inside mobile apps. Cellular internet remains quite expensive in many cases, especially when you’re travelling abroad. That’s why people often use Wi-Fi in airports, cafes and hotels without paying much attention to its security. In case studies, performed by our experts in Sao Paulo just before the World Cup to discover what kind of encryption people use on their wireless networks, we found that one in four networks use open standard (no encryption).
26% of Wi-Fi networks in Sao-Paulo are insecure. You must take care especially when using mobile apps.
Tweet
If you use open standard, anyone can sniff your traffic and see what data are you sending. If you’re using WEP, encryption could be cracked in no more than 5 minutes. Many networks around the world can be sniffed out by bad guys in a matter of seconds.
Our recommendation is to only connect to networks that use WPA.
The story is different when using mobile apps. You really don’t know what protocol app uses. Security experts discovered that many applications still use open protocol for internal communication with their servers – i.e. HTTP instead of HTTPS, and those connections are vulnerable to session hijacking, password stealing and content eavesdropping. For example, if you’re IM’ing, people can see plaintext of your conversations. And I’m not making stuff up, it’s a real problem that persists in mobile applications. Even Google, Facebook or Twitter had some problems with SSL missing in their mobile apps in 2011. Till summer 2012, WhatsApp, a hugely popular IM mobile app, was transmitting all content unencrypted. If someone still uses Yahoo messenger or ICQ, I have bad news for them – it’s still using plaintext protocol so all chats are unencrypted and could be easily eavesdropped over open Wi-FI. It’s hard to imagine how many applications still have plaintext protocol inside, if even some A-level companies don’t implement encryption yet.
If we get more technical, many mobile apps don’t warn users about problems with SSL certificates, making it almost impossible to spot man-in-the-middle attacks.
Of course it would be easy to give simple advice like “don’t use mobile apps for anything sensitive” – but it’s hard to follow this advice. Following that, you’re effectively putting yourself back in the 20th century. So I would recommend a somewhat less radical approach:
- Use 3G/4G service instead of Wi-Fi in public places, if you have such opportunity;
- Always prefer encrypted Wi-Fi connections (WPA2);
- Enforce VPN usage on your mobile device;
- Avoid doing sensitive stuff like online banking in public environments and via untrusted networks (which are effectively all networks except properly configured home and office networks).
 Android
Android


 Tips
Tips