According to Kaspersky Lab “Spam and phishing in 2016” report, about 20% of all spam emails in Q4 2016 distributed ransomware Trojans
According to Kaspersky Lab “Spam and phishing in 2016” report,about 20% of all spam emails in Q4 2016 distributed ransomware Trojans.
The Kaspersky Lab spam report also identified the following trends in 2016:
- The volume of spam emails in 2016 increased to 58.31% of overall email traffic, a rise of 3.03% on 2015
- The US remained the biggest source of spam (12.08%), with second place taken by Vietnam (10.32%), and India in third (10.15%)
- Germany remained in first place among the countries targeted by malicious mailshots (14.13%). The second and third places were occupied by Japan (7.59%) and China (7.32%), both of which were outside the top 10 in 2015
- 15.29% of unique users were attacked by phishers
- In 2016 the average proportion of phishing attacks against customers of financial institutions was 47.48%, up from 34.33% in 2015 and 28.74% in 2014
- Trojan.Win32.Bayrob was used to send out spam and steal personal data, and was the most popular malware family distributed via email
Hot spam topics of the year: sport and terrorism
Phishers, predictably, could not pass on the opportunity presented by the most high-profile event of the year – the Olympic Games in Brazil. Fraudulent spam also exploited other major sporting events, including the European Football Championship, as well as the upcoming World Cups in 2018 and 2022. Spammers sent out fake lottery win notifications related to these events. The lottery was supposedly run by an official organization and the recipient’s address had been randomly selected from millions of other addresses. This theme was also used in malicious spam. In this case, the emails included a ZIP archive attachment with a JavaScript downloader detected by Kaspersky Lab as Trojan-Downloader.Script.Generic. This malware, in turn, downloaded other malicious software to the victims’ computers.
The subject of terrorism, which has remained an important global issue in recent years, especially around the tense situation in Syria, was also exploited in spam mailings. Numerous so-called Nigerian letters, leveraging the problem of terrorism and refugees, were sent to users on behalf of both state organization employees and individuals. The details of the stories may have differed, but the senders’ intentions were the same – to get the recipient’s attention with promises of large sums of money and make them join a conversation.
Chinese entrepreneurs on the rise
Spam advertisements became very popular with small and medium businesses in China in 2016. The text of a typical spam message generally began with an impersonal greeting to the recipient, followed by the name and surname of a factory manager. Often, the email described the merits of the company, its achievements and types of certification.
Chinese businesses have not started to use new, more targeted, convenient and less intrusive advertising platforms, such as social networking sites, and Kaspersky Lab researchers believe this may be because social networks in China are mainly internal, with global giants such as Facebook not being permitted. As a result, Chinese entrepreneurs have far fewer legal means of entering the international market, even though the state has passed its own anti-spam law, which is one of the strictest in the world.
Ransom is king
In 2016, a huge amount of malicious spam was recorded. The absolute leaders in spam were the Trojan downloaders that download ransomware to a victim’s computer. The most popular were mass spam mailings sent out to infect user computers with the Locky encryptor. However, other ransomware such as Petya, Cryakl and Shade were also widespread.
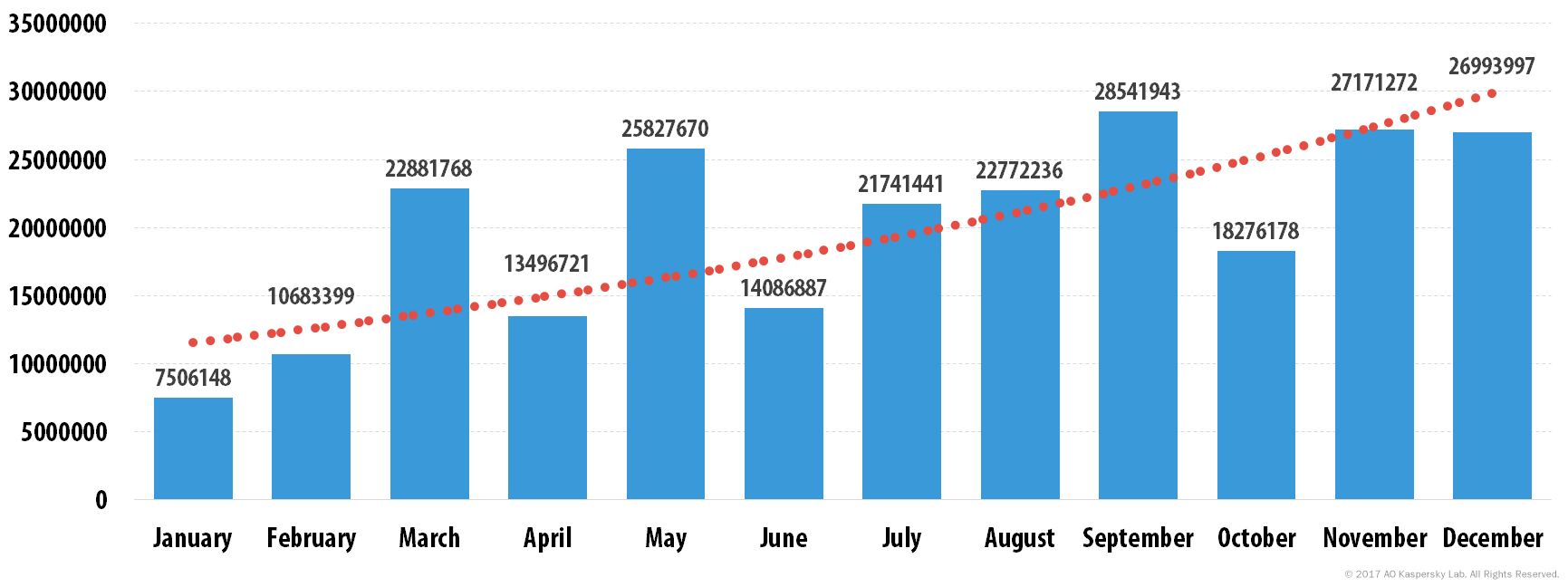
Quantity of malicious spam emails, 2016
The number of malicious programs began to increase in December 2015 and continued to grow in waves throughout the following year. The sharp falls were mainly caused by the fact that cybercriminals temporarily disabled the Necurs botnet, responsible for the majority of spam spreading Locky.
“2016 saw a variety of changes in spam flows, with an increase in the number of malicious mass mailings containing ransomware being the most significant. Such an extensive use of ransomware may be due to the availability of this sort of malware on the black market. Currently, cybercriminals can not only rent a botnet to send out spam, they can also use so-called Ransomware-as-a-Service. This means that the attacker may not be a hacker in the traditional sense, and may not even know how to code. In 2017 the volume of malicious spam is unlikely to fall,” said Darya Gudkova, Spam Analyst Expert at Kaspersky Lab.
Read more about spam and phishing in 2016 on Securelist.com
