A multistep phishing scheme aimed at employees that process financial documentation was discovered by Kaspersky. The scheme begins when victims receive an email from the legitimate address of an auditing firm. This initial interaction is intended to make the recipient less suspicious: like a preparatory step to ease into the main fraudulent activity. Then a notification from the Dropbox service follows, containing malicious links to archives where cybercriminals have uploaded phishing files designed to steal credentials.
The first step involves victims receiving emails purportedly from a legitimate auditing firm. These emails are sent from authentic address, which has most likely been hijacked by attackers. They employ social engineering tactics to lower victims’ guard and prepare them to receive a Dropbox archive.
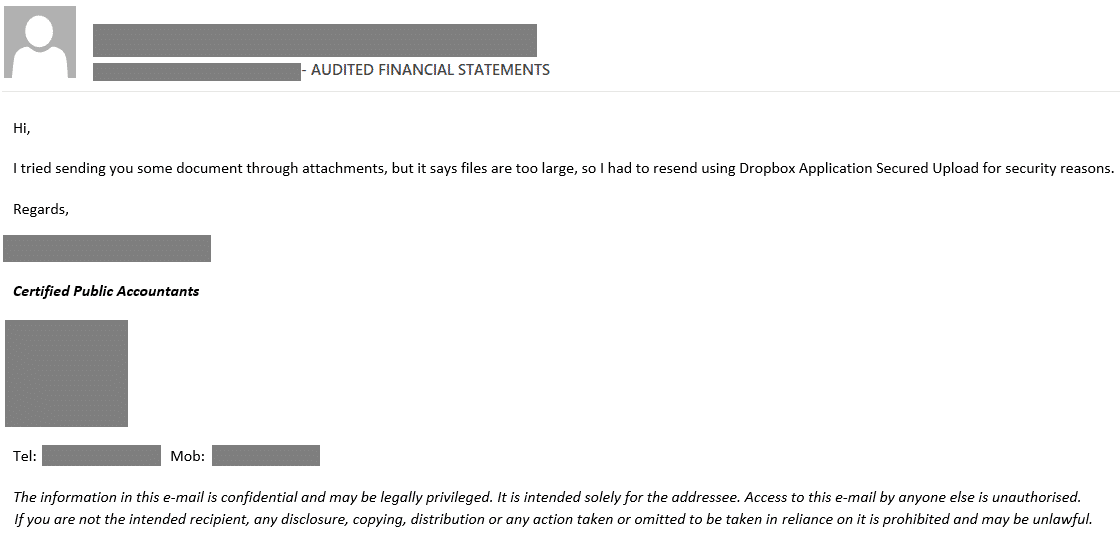
The first step in the scheme: the victim received an email from an alleged “auditor”
“The email appears legitimate from both a human standpoint and in terms of protection software. It contains a plausible cover story that an official audit company has information for the recipient, complete with a disclaimer regarding sharing confidential information. In addition, the email contains no links or attachments and originates from an easily searchable company address, making it nearly impossible for a spam filter to detect”, explains Roman Dedenok, a security expert at Kaspersky.
The only suspicious trait in this email is that the sender uses “Dropbox Application Secured Upload”. This service doesn’t exist. Although files uploaded to Dropbox can be password-protected, nothing more can be done.
Following this email, the perpetrators send their victims an official Dropbox notification. If the recipient is already primed to respond by the initial message, there is a higher likelihood they’ll follow the link to review the document.
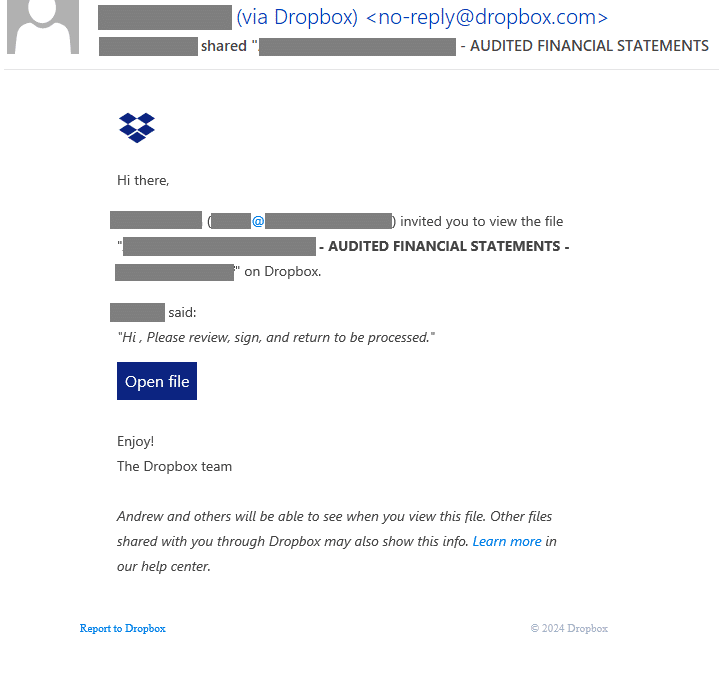
Dropbox notification
Clicking on the link reveals a blurred document with an authentication window on top of it. The document acts as a large button, with its entire surface being a malicious link. Upon clicking, the user will see a form requesting their corporate login and password: credentials that cybercriminals seek to steal using this multistep scheme.
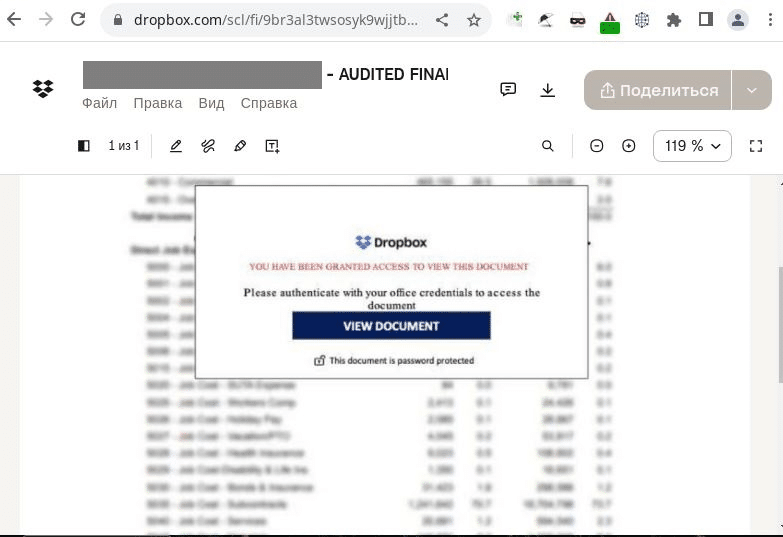
The malicious PDF file uploaded to Dropbox, mimicking an authentication request.
These attacks are considered targeted and were observed by Kaspersky in isolated instances. The scheme is described in detail in the Kdaily post. To stay protected, it is advisable to warn employees and encourage vigilance. Here are a few pieces of advice:
- Provide your staff with basic cybersecurity hygiene training. Conduct a simulated phishing attack to ensure that they know how to distinguish phishing emails.
- Overall, all company employees should remember to input their work password only on sites owned by their organization. Neither Dropbox nor external auditors can know and need your work password.
- As perpetrators constantly devise more sophisticated schemes to steal corporate account data, we recommend implementing real-time protection, threat visibility, investigation and response solutions, such as Kaspersky Next product line.
