Attackers are increasingly targeting Windows by exploiting vulnerable drivers, according to Kaspersky experts. In the second quarter of 2024, the number of systems attacked using this technique increased by nearly 23% compared to the first quarter. Vulnerable drivers may be exploited for a wide range of attacks, including ransomware and Advanced Persistent Threats (APTs).
Cyberattacks that utilize vulnerable drivers are known as BYOVD (Bring Your Own Vulnerable Driver). They allow threat actors to attempt to disable security solutions on a system and escalate privileges, enabling them to carry out various malicious activities, such as installing ransomware or establishing persistence for espionage or sabotage, particularly if an Advanced Persistent Threat (APT) group is behind the attack.
Kaspersky reports that this attack technique accelerated in 2023 and is currently gaining momentum, with a potential impact on both individuals and organizations. In Q2 2024, the number of systems attacked with the BYOVD technique increased by almost 23% compared to the previous quarter.
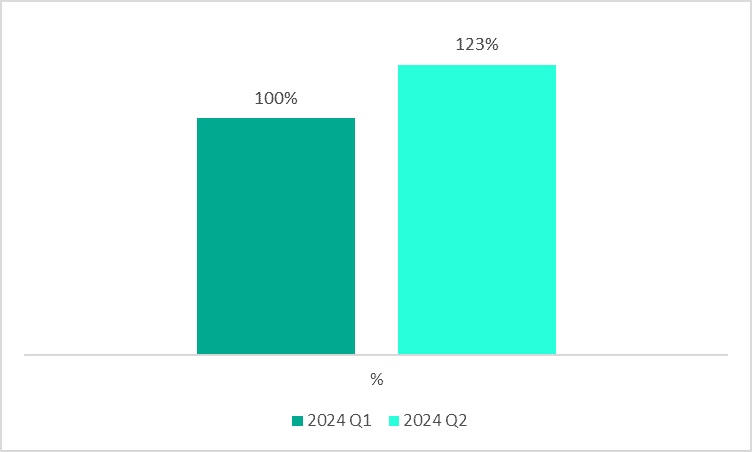
Dynamics in attacks exploiting vulnerable drivers
“While the drivers themselves are legitimate, they may contain vulnerabilities. These vulnerabilities can then be exploited for malicious purposes. Perpetrators use various tools and methods to install a vulnerable driver on the system. Once the operating system loads this driver, the attacker can exploit it to circumvent OS kernel security boundaries for their own goals,” explains Vladimir Kuskov, Head of Anti-Malware Research at Kaspersky.
One concerning aspect of this trend is the proliferation of tools that exploit vulnerable drivers –they can be found online. While relatively few of these tools exist in 2024 – only 24 projects have been published since 2021– Kaspersky experts observed an increase in the number of these tools being published online last year. “Although nothing really stops threat actors from developing their own private tools, the publicly available ones eliminate the need for the specific skills required to research and exploit vulnerable drivers. In 2023 alone, we identified approximately 16 new tools of this nature, marking a substantial increase from the mere one or two we observed in previous years. Given this rise, it is highly advisable to implement robust protective measures for any system”, elaborates Vladimir Kuskov.
To counter threats related to vulnerable driver exploitation, the following measures are effective:
- Thoroughly understand your infrastructure and closely monitor its assets, focusing on the perimeter.
- To protect the company against a wide range of threats, use solutions from the Kaspersky Next product line. It provides real-time protection, threat visibility, investigation and response capabilities of EDR and XDR for organizations of any size and industry, as well as safeguarding systems against vulnerable driver exploitation.
- Implement a Patch Management process to detect vulnerable software within the infrastructure and promptly install security patches. Solutions like Kaspersky Endpoint Security and Kaspersky Vulnerability Data Feed can assist in this regard.
- Conduct regular security assessments to identify and patch vulnerabilities before they become an entry point for an attacker.
Read more on vulnerabilities and exploits threat landscape in Q2 2024 on Securelist. For a deeper immersion in the ever-evolving world of cyber threats and insightful networking, join Kaspersky’s Security Analyst Summit (SAS), which will take place for the sixteenth time from October 22-25, 2024, in Bali.
