Kaspersky has detected an online fraud campaign aimed at stealing cryptocurrency and sensitive information by exploiting popular topics such as web3, crypto, AI, online gaming, and beyond. Targeting individuals worldwide, the campaign is believed to be orchestrated by Russian-speaking cybercriminals and spreads info-stealing and clipper malware.
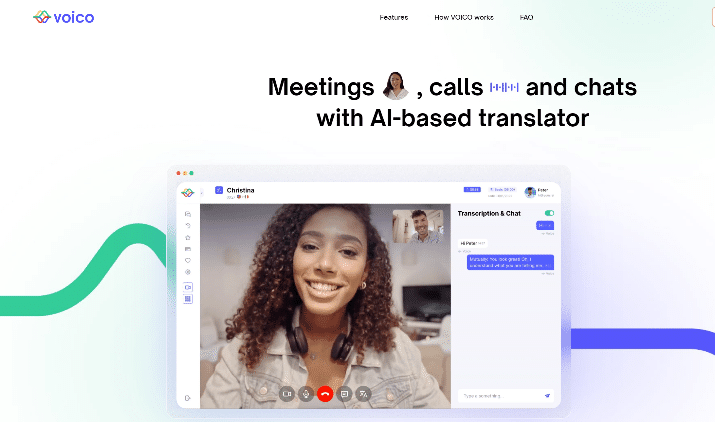
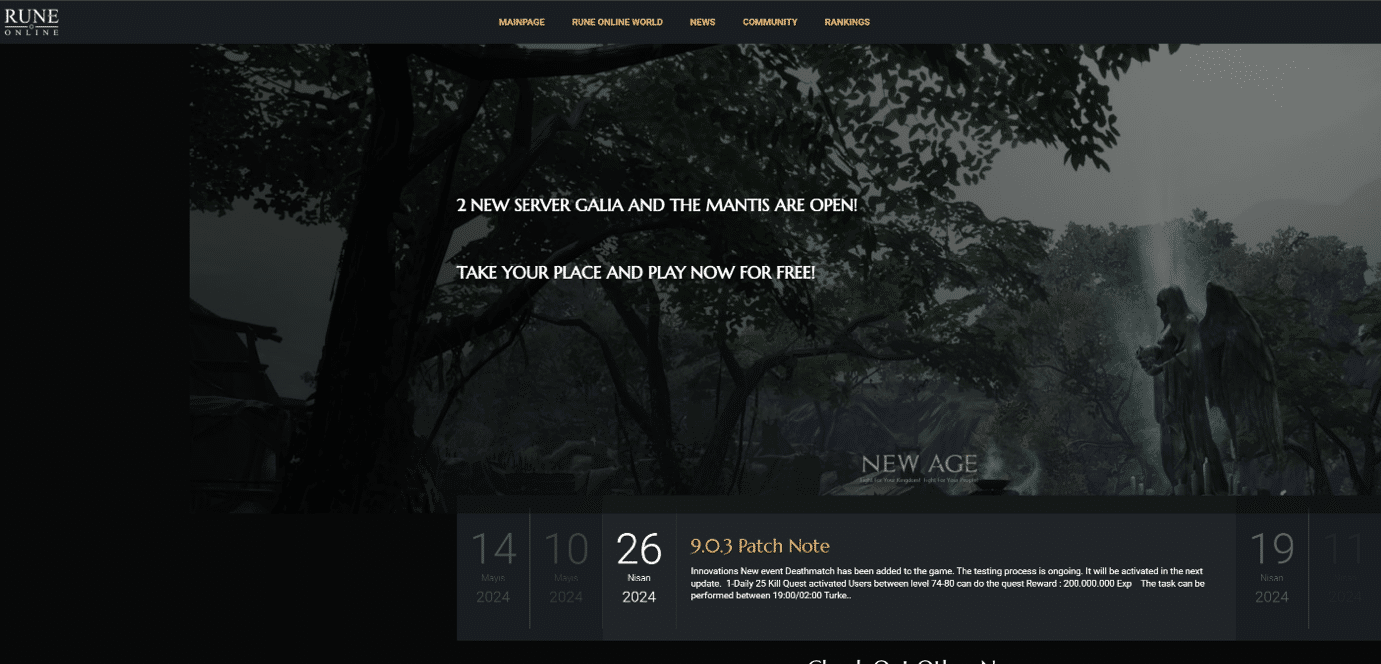
Kaspersky Global Emergency Response Team (GERT) has detected a fraud campaign targeting Windows and macOS users worldwide, aimed at stealing cryptocurrency and personal information. The attackers exploit popular topics to lure victims with fake websites that closely mimic the design and interface of various legitimate services. In recent cases, these sites have imitated a crypto platform, an online role-playing game, and an AI translator. Although there are minor differences in elements of the malicious sites, like the name and URL, they appear polished and sophisticated, increasing the likelihood of a successful attack.

|
 |
|
|
| Fake websites created as a part of Tusk campaign, mimicking legitimate crypto and AI services, and an online game | |
Victims are lured into interacting with these fake setups through phishing. The websites are designed to trick individuals into giving away sensitive information, such as crypto-wallet private keys, or downloading malware. The attackers can then either connect to the victims’ cryptocurrency wallets through the fake site and drain their funds, or steal various credentials, wallet details, and other information using the info-stealing malware.
“The correlation between different parts of this campaign and their shared infrastructure suggests a well-organized operation, possibly linked to a single actor or group with specific financial motives,” says Ayman Shaaban, Head of Incident Response Unit, Global Emergency Response Team, Kaspersky. “In addition to the three sub-campaigns targeting crypto, AI, and gaming topics, our Threat Intelligence Portal has helped to identify infrastructure for 16 other topics — either older, retired sub-campaigns or new ones not yet launched. This demonstrates the threat actor’s ability to swiftly adapt to trending topics and deploy new malicious operations in response. It underscores the critical need for robust security solutions and enhanced cyber literacy to protect against evolving threats.”
Kaspersky discovered strings in the malicious code sent to the attackers' servers in Russian. The word “Mammoth” (rus. “Мамонт”), slang used by Russian-speaking threat actors to refer to a “victim”, appeared in both the server communications and malware download files. Kaspersky dubbed the campaign “Tusk” to emphasize its focus on financial gain, drawing an analogy to mammoths hunted for their valuable tusks.
The campaign is spreading info-stealer malware such as Danabot and Stealc, as well as clippers such as an open-source variant written in Go (the malware varies depending on the topic within the campaign). Infostealers are designed to steal sensitive information like credentials, while clippers monitor clipboard data. If a cryptocurrency wallet address is copied to the clipboard, the clipper substitutes it with a malicious address.
Malware loader files are hosted on Dropbox. Once victims download them, they encounter user-friendly interfaces that serve as covers for the malware, prompting them to either log in, register or simply remain on a static page. In the meantime, the remaining malicious files and payloads are automatically downloaded and installed onto their system.
 |
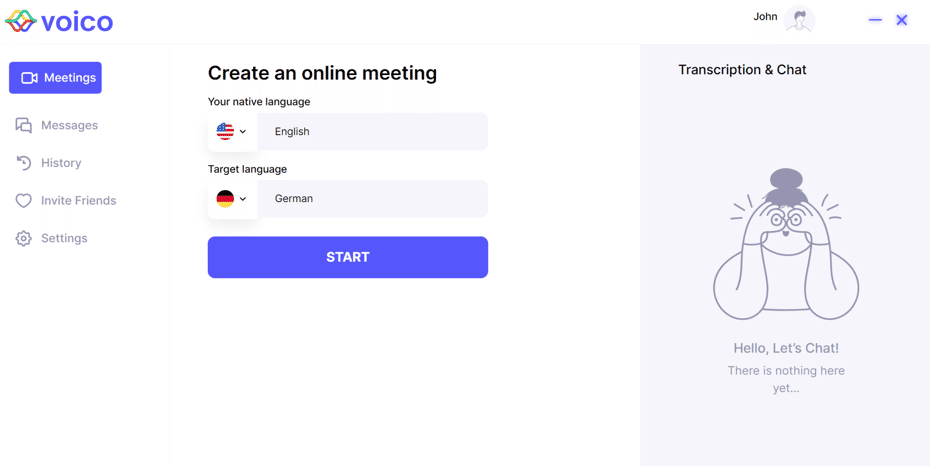 |
| User interface of the malware downloader within the campaign targeting gamers | User interface of the malware downloader within the campaign targeting users of AI-translators |
The detailed technical breakdown of the campaign will be published on Securelist on August 16, 2024. For a deeper immersion in the ever-evolving world of cyber threats and insightful networking, join Kaspersky’s Security Analyst Summit (SAS), which will take place for the sixteenth time from October 22-25, 2024, in Bali.
To mitigate against Tusk-related cyberthreats, Kaspersky suggests the following measures:
- Check if the credentials for your company’s devices or web applications have been compromised by infostealers via dedicated Kaspersky Digital Footprint Intelligence landing page.
- To guard against data-stealing malware and crypto-threats, individuals are advised to use a comprehensive security solution for any device, such as Kaspersky Premium. This will help prevent infections and alert them to dangers, such as suspicious sites or phishing emails that can be an initial vector for infection. And all new malicious samples from the Tusk campaign can already be detected by Kaspersky products.
- Invest in additional cybersecurity courses for your staff to keep them up to date with the latest knowledge. Kaspersky Expert training on Windows Incident Response allows even seasoned specialists to train in incident response to identify the most complex attacks and brings concentrated knowledge from the company’s Global Emergency Response Team (GERT) experts.
- Since info-stealing malware usually targets passwords, use a Kaspersky Password Manager to make using secure passwords easier.
