In Q2 2017, cybercriminals involved in spam distribution tried to capitalise on public fears when the WannaCry ransomware epidemic struck in May.
In Q2 2017, cybercriminals involved in spam distribution tried to capitalise on public fears when the WannaCry ransomware epidemic struck in May. Knowing that there are lots of people out there infected with this ransomware, and searching for ways to get their encrypted data back, fraudsters sent out spam and phishing emails, offering users different services to fight against the epidemics. This is one of the key findings of Kaspersky Lab’s “Spam and phishing in Q2 2017” report.
The WannaCry ransomware attack affected more than 200,000 computers across the globe, resulting in massive panic, and spammers instantly capitalised on the opportunity. Researchers detected a large amount of messages offering services such as protection from WannaCry attacks, data recovery, and, moreover, educational workshops and courses for users. In addition, spammers successfully implemented a traditional scheme of fraudulent offers to install software updates on affected computers. However, links were redirecting users to phishing pages, where the personal data of victims would have been stolen.
One of the main trends in the past three months is the number of mass mailings targeted at corporate networks. Based on Kaspersky Lab research, these have expanded since the beginning of the year. Spammers began to widely disguise malicious mailings as corporate dialogues, by using the identities of corporate mail services, including real signatures, logos and even banking information. In archives attached to the email, cybercriminals sent out exploit packages targeted at stealing FTP, email and other passwords. Kaspersky Lab experts highlight that most attacks on the corporate sector have financial goals.
In addition, in the second quarter of the year researchers detected a growth in number of mass mailings with malicious Trojans, sent on behalf of international delivery services. Spammers were sending shipping reports with information about non-existent parcel deliveries. With the aim to infect computers or to steal personal credentials, criminals were found spreading download links with malware, including the banking Trojan Emotet, which was first detected back in 2014. Overall, the volume of malicious mass mailings have increased by 17 per cent, according to the new Kaspersky Lab report.
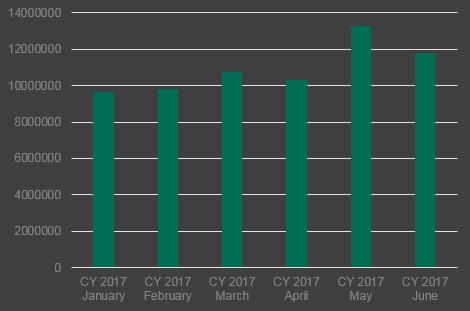
The number of email antivirus detections, Q1 2017 vs Q2 2017
“During the second quarter of the year, we have seen that the main trends in spam and phishing attacks have continued to grow. The use of WannaCry in mass mailings proves that cybercriminals are very attentive and reactive to international events. Moreover, cybercriminals have started to focus more on the B2B sector, seeing it as lucrative. We expect this tendency will continue to grow, and the overall amount of corporate attacks and their variety will expand”, said Darya Gudkova, Spam Analyst Expert at Kaspersky Lab.
Other important trends and statistics in Q2, highlighted by Kaspersky Lab researchers, include the following:
- The average amount of spam has increased up to 56.97 per cent. Vietnam became the most popular source of spam, overtaking the U.S. and China. The top 10 countries include Russia, Brazil, France, Iran and the Netherlands.
- The Necurs botnet is still active. However, the experts spotted a decrease in the volume of spam sent from this botnet, and its instability.
- The country most targeted by malicious mailshots was Germany. The leader of the previous period, China, came second, followed by U.K., Japan and Russia. Other popular targets include Brazil, Italy, Vietnam, France and the U.S.
- The Kaspersky Lab Anti-Phishing system was triggered 46,557,343 times on the computers of Kaspersky Lab users. The largest percentage of affected users were in Brazil (18.09 per cent). Overall, 8.26 per cent unique users of Kaspersky Lab products worldwide were attacked by phishing.
- As in Q1, the main targets of phishing attacks remained the same and were primarily from the financial sector: banks, payments services and online stores.
Read more about spam and phishing in Q2 2017 on Securelist.com.
Kaspersky Lab recommends home users install a reliable secure solution to detect and block spam and phishing attacks, such as Kaspersky Total Security.
Businesses are recommended to use security solutions with a dedicated functionality aimed at malicious attachments and spam. Small businesses can protect themselves with Kaspersky Small Office Security, Kaspersky Endpoint Security Cloud which spots and blocks emails with spam.
Larger companies can benefit from real-time cloud-assisted anti-spam scanning of all messages on Microsoft® Exchange and Linux-based email servers — with the Kaspersky Security for Mail Server application included with Kaspersky Total Security for Business.
