With more and more people using their smartphones and tablets to surf the web, update social networking sites and shop & bank online, cybercriminals and malware are increasingly targeting mobile devices – with new smartphone threats and mobile threats.
Android devices are ‘under attack’
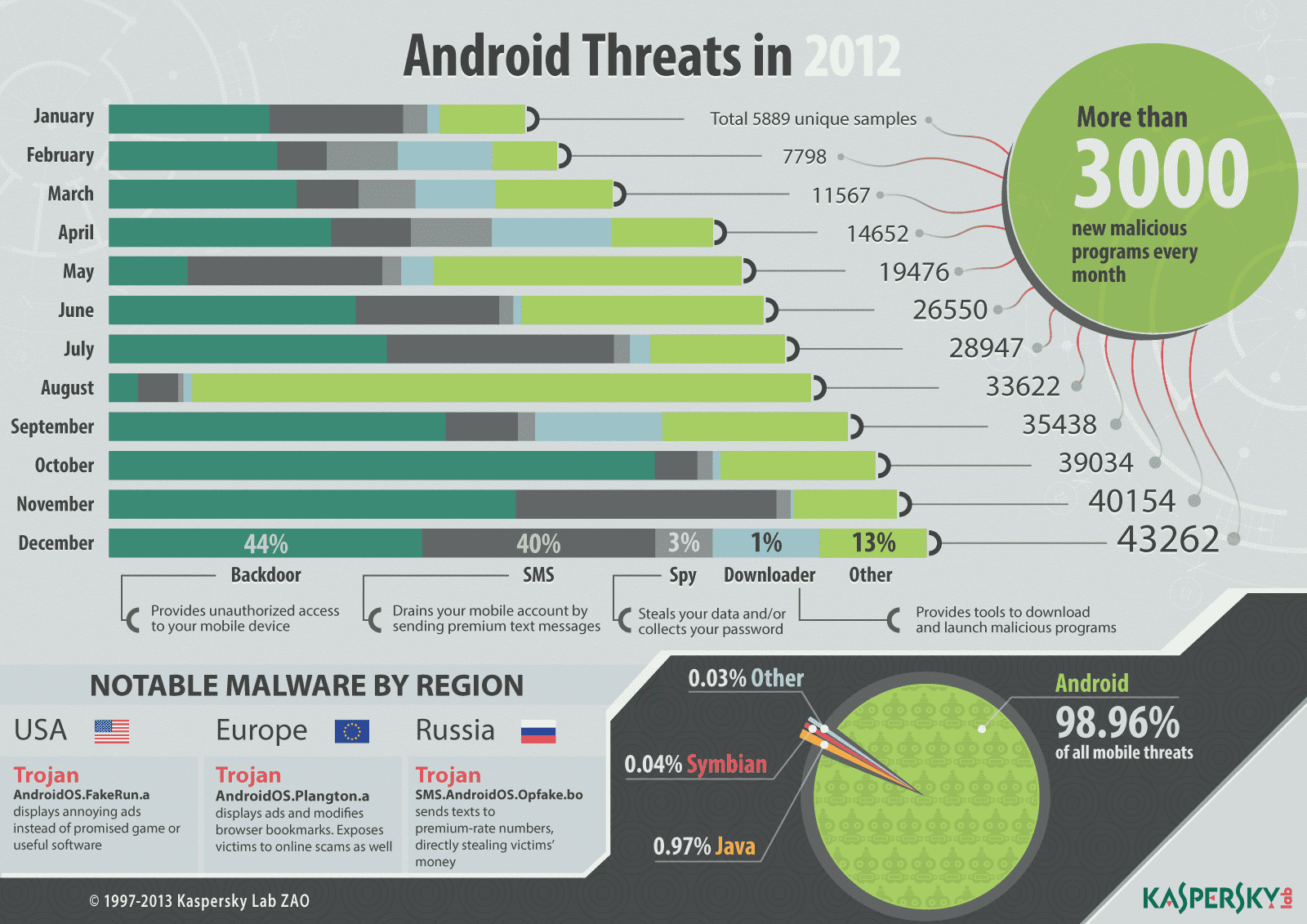
Throughout 2012, 99% of all mobile malware detected by Kaspersky was designed to target the Android platform. During the year, Kaspersky’s Internet security experts identified more than 35,000 malicious Android programs.
The reasons for the huge growth in Android malware are:
- The Android platform has become the most widespread operating system (OS) for new smartphones – it has over 70% market share.
- The open nature of the Android OS, the ease with which apps can be created and the wide variety of (unofficial) application markets all have an influence on security.
What types of threats are affecting Android devices?
The most widespread malicious objects detected on Android smartphones can be divided into three main groups:
- SMS Trojan viruses
- Advertising modules
- Exploits – to gain root access to smartphones
Malware has been found in app stores. During 2012, Kaspersky detected malicious programs in Google Play, the Amazon app store and other third-party app stores.
Online banking security risks for Android users
European and American banks and e-pay systems offer a variety of ways to protect users’ transactions – including authentication using e-tokens, one-time passwords, confirmation of transactions through codes sent to the phone and more.
However, cybercriminals are developing programs that bypass these measures. For example, the Zitmo family of programs is designed to attack a user’s mobile phone and can bypass the two-factor authentication systems used by European banks. These mobile malicious programs work in tandem with Zbot (ZeuS):
- First Zbot steals the username and password – to enter the online banking system from the infected computer.
- Then, during a money transfer, Zitmo – Zbot’s mobile counterpart – takes over and forwards the transaction authorisation code (TAN) to the cybercriminals.
Related Products:
Other articles and links related to malware and security